Get started by creating custom policies as described in the link from below:

Fig 1 - Custom policies added in the B2C
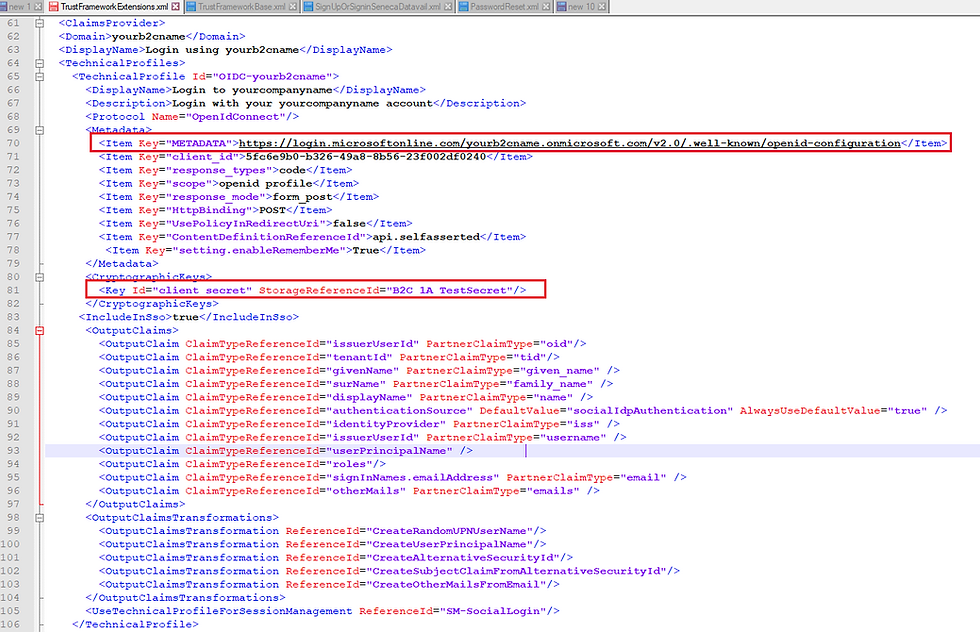
Fig 2 - The sign-in policy uses an application secret stored as a key into the B2C
Read the article from below to see how to set-up a REST API claims exchanger and return roles information into the token:

Fig 3 - The policy makes a call to an Azure function to pass the user GUID as a parameter and retrieve the roles from the server as a claim added into the token
Create a certificate for your custom domain, create a key for the application to store the certificate, and bind the certificate to the Azure function custom domain and SSL configuration.
Make sure the Azure function's configuration setting is set up to require the use of this certificate. In this way, the function can be called just by the policy.

Fig 4 - Azure function configuration requires the validation of the certificate when calling the function
Details about the Azure function can be found in the blog from below:

Comentarios